access control systems security identity management and trust models

Tài liệu Control Systems Simulation using Matlab and Simulink pptx
Ngày tải lên :
12/12/2013, 07:15
... order system
6 “Hands-on” Design of Control Systems
“Hands on Design systems refers to directly working with the system to be controlled and trying
a variety of controllers and control parameters.
6.1 ... (u)whichwillactuponthesystem
and bring it nearer to the desired value.
We are interested in three types of controllers:
6.2.1 Proportional Control (P -control) :
This is the simplest type of continuous control law. The controller ... required.
Control Systems Simulation
Using Matlab and Simulink
1 Introduction
In ME134, we will make extensive use of Matlab and Simulink in order to design, analyze and
simulate the response of control...
- 10
- 648
- 3

Tài liệu Control Systems Simulation using Matlab and Simulink doc
Ngày tải lên :
22/12/2013, 21:18
... amplitudes in bands less than ‘1X’ and ‘1X’
A1: the ratio of peak amplitudes in band ‘1X’ and its initial record (in good condition)
A2: the ratio of peak amplitudes in bands ‘2X’ and ‘1X’
A3: ... applications
such as medical diagnosis [Slowinski, 1992], control algorithm acquisition and process control [Mrozek,
1992], and structural engineering [Arciszewski and Ziarko, 1990]. However, most literature ... based
on rough sets and a decision-tree learning methodology, and the predecessor of RClass
*
, for inductive
learning under noisy environment.
Approximation space and the lower and upper approximations...
- 21
- 513
- 0

BYPASSING NETWORK ACCESS CONTROL SYSTEMS potx
Ngày tải lên :
14/03/2014, 20:20
... network security and regulation
compliance. By providing comprehensive network visibility and access control, Insightix customers reduce
the time, cost and complexity associated with IT management. ... NAC Systems
Abstract
The threat of viruses, worms, information theft and lack of control of the IT infrastructure has lead
companies to implement security solutions to control the access ... elements and users to connect to the network.
This set of technologies is termed by many as Network Access Control (NAC) - a set of technologies and
defined processes aimed at controlling access...
- 30
- 402
- 1

Knowledge Management and Specialized Information Systems
Ngày tải lên :
23/01/2013, 11:06
... Knowledge
Management)
o Effective KMS dựa trên việc học kiến thức mới và thay đổi thủ tục
và hướng tiến cận như một kết quả (Is based on learning new
knowledge and changing procedures and approaches ... conclusions and works backward to
supporting facts)
o Forward chaining
Bắt đầu với những sự kiện và làm việc tiến tới kết luận
d. Yếu tố giải thích (The Explanation Facility)
Chương 11: Knowledge Management ... luận
d. Yếu tố giải thích (The Explanation Facility)
Chương 11: Knowledge Management and Specialized Information Systems
1. Nguyên lý và mục tiêu học tập
Quản lý tri thức là cho phép các tổ chức...
- 15
- 1.6K
- 9

Tài liệu Data Management and Access Products ppt
Ngày tải lên :
10/12/2013, 17:15
... Assembly
Data Management and Access Products
17
12/02 • 517
Data Management and Access Products
www.adc.com • +1-952-938-8080 • 1-800-366-3891
EIA-232/V.24 PatchMate
™
EIA-232/V.24 has been a long standing ... Receptacle/Female Connector
2
12/02 • 517
Data Management and Access Products
www.adc.com • +1-952-938-8080 • 1-800-366-3891
Data Management and Access
Components
Assemblies
Prepackaged combinations ... Color
Black
Black
Black
Black
Black
Red
Grey
Red
Red
12/02 • 517
Data Management and Access Products
www.adc.com • +1-952-938-8080 • 1-800-366-3891
Data Management and Access Products
Table of Contents
General Introduction...
- 68
- 600
- 0
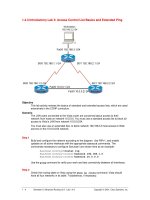
Tài liệu Access Control List Basics and Extended Ping ppt
Ngày tải lên :
21/12/2013, 19:15
... to both standard and extended access lists:
Two-step process. First, the access list is created with one or more access- list
commands while in global configuration mode. Second, the access list ... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc.
Access Control List Basics
Access Control Lists (ACLs) are simple but powerful tools. When the access list is
configured, each statement ... for. The deny command discards
packets matching the criteria on that line.
Two important keywords that can be used with IP addresses and the access list
command are any and host. The keyword...
- 4
- 456
- 3

Tài liệu Access Control List Basics and Extended Ping doc
Ngày tải lên :
21/12/2013, 19:15
... to both standard and extended access lists:
Two-step process. First, the access list is created with one or more access- list
commands while in global configuration mode. Second, the access list ... v2.0 - Lab 1.4.3 Copyright 2001, Cisco Systems, Inc.
Access Control List Basics
Access Control Lists (ACLs) are simple but powerful tools. When the access list is
configured, each statement ... you will configure an extended ACL to block access to a Web server. Before you
proceed, issue the no access- list 50 and no ip access- group 50 commands
on the Vista router to remove the ACL...
- 4
- 591
- 3


Sap Solutions For Governance Risk And Compliance And Grc Access Control 3 doc
Ngày tải lên :
05/03/2014, 19:20
...
Access Management
Effective
Management Oversight
and Audit
Access Controls
SAP GRC
Access Control
© SAP AG 2007, SAP Skills 2007 Conference / G3 / 37
SAP GRC Access Control 5.3
SAP GRC Access ... Process Control: Centralized Control
Management
Centralized Control
Management
One system for managing
automated and manual
controls
System can manage
–
Financial Control
–
Operational Controls
–
... Control 5.3
SAP GRC Access Control branding and single launchpad for all 4 access control capabilities
Roadmap
SAP GRC Access Control 5.3
Q1 2008 (AC 5.3)
Access Control
5.2 SP3
Language Translations
•
...
- 146
- 768
- 0

Management Planning Guide for Information Systems Security Auditing pot
Ngày tải lên :
05/03/2014, 21:20
... inadequate access controls
Ability to analyze and evaluate an organization’s access controls and identify the strengths and
weaknesses
Skills to review security software reports and identify access control ... reports and elsewhere resulted from the lack
of fundamental computer security controls: information security management program,
physical and logical access controls, software change controls, ... the elements of a good security program
Ability to analyze and evaluate an organization’s security policies and procedures and identify their
strengths and weaknesses
Access control
Knowledge across...
- 66
- 477
- 0

INTERNATIONAL PERSPECTIVES ON WATER QUALITY MANAGEMENT AND POLLUTANT CONTROL doc
Ngày tải lên :
07/03/2014, 11:20
... D.M. Anderson, “Approaches to monitoring, control and management of harmful al‐
gal blooms (HABs),” Ocean & Coastal Management, 2009, p. 342-7.
[23] W.A. Kratz, and J. Myers, “Nutrition and ... cyanobacteria, and phytoplankton by utilizing the
bacteria-specific 16s rRNA gene primers 27FB and 785R, PSf and PSr, and CPC1f and
CPC1r, respectively. Specific primers were used after phytoplankton and ... while handling, filling, closing, labeling and packaging the containers for storage and
transport.
Two people collected the samples; one was designated “dirty hands” and the other “clean
hands”....
- 130
- 537
- 0
- access control and security systems integration
- access control and security management systems
- access control and security systems jobs
- access control and security management
- access control and security systems
- access control systems security identity management and trust models
- access control systems security identity management and trust models by messaoud benantar
Tìm thêm:
- hệ việt nam nhật bản và sức hấp dẫn của tiếng nhật tại việt nam
- xác định các mục tiêu của chương trình
- xác định các nguyên tắc biên soạn
- khảo sát các chuẩn giảng dạy tiếng nhật từ góc độ lí thuyết và thực tiễn
- khảo sát chương trình đào tạo của các đơn vị đào tạo tại nhật bản
- khảo sát chương trình đào tạo gắn với các giáo trình cụ thể
- xác định thời lượng học về mặt lí thuyết và thực tế
- tiến hành xây dựng chương trình đào tạo dành cho đối tượng không chuyên ngữ tại việt nam
- điều tra đối với đối tượng giảng viên và đối tượng quản lí
- điều tra với đối tượng sinh viên học tiếng nhật không chuyên ngữ1
- khảo sát thực tế giảng dạy tiếng nhật không chuyên ngữ tại việt nam
- khảo sát các chương trình đào tạo theo những bộ giáo trình tiêu biểu
- nội dung cụ thể cho từng kĩ năng ở từng cấp độ
- xác định mức độ đáp ứng về văn hoá và chuyên môn trong ct
- phát huy những thành tựu công nghệ mới nhất được áp dụng vào công tác dạy và học ngoại ngữ
- mở máy động cơ lồng sóc
- mở máy động cơ rôto dây quấn
- các đặc tính của động cơ điện không đồng bộ
- hệ số công suất cosp fi p2
- đặc tuyến hiệu suất h fi p2








